Build Cross-Platform Apps Using Your Favorite Web Stack
Reasonably Secure Edition
What is an App really?
| > Application software |
| > Mobile app, software designed to run on smartphones and other mobile devices |
| > Web application or web app, software designed to run inside a web browser |
Web
Native
Simple
Tauri
The Tech Stack
WebViews
To Bundle, or Not to Bundle?
Web vs Native
Threat Model
What is a Trust Boundary?
Trust boundary is a term used in computer science and security which describes a boundary where program data or execution changes its level of "trust," or where two principals with different capabilities exchange data or commands. (Wikipedia)
Trust Boundaries
IPC
Communication across Trust Boundaries
Tauri Commands
Rust Backend
#[tauri::command]
fn my_greeting(message: String) -> String {
format!("{message} from Rust!")
}
JavaScript Frontend
invoke('my_greeting'{ message: 'Hello!' }).then((greeting) => console.log(greeting))
Recap
Getting Beyond Basics
Hostile Environment
You can't trust anything!
Sandboxing
Finding The Balance
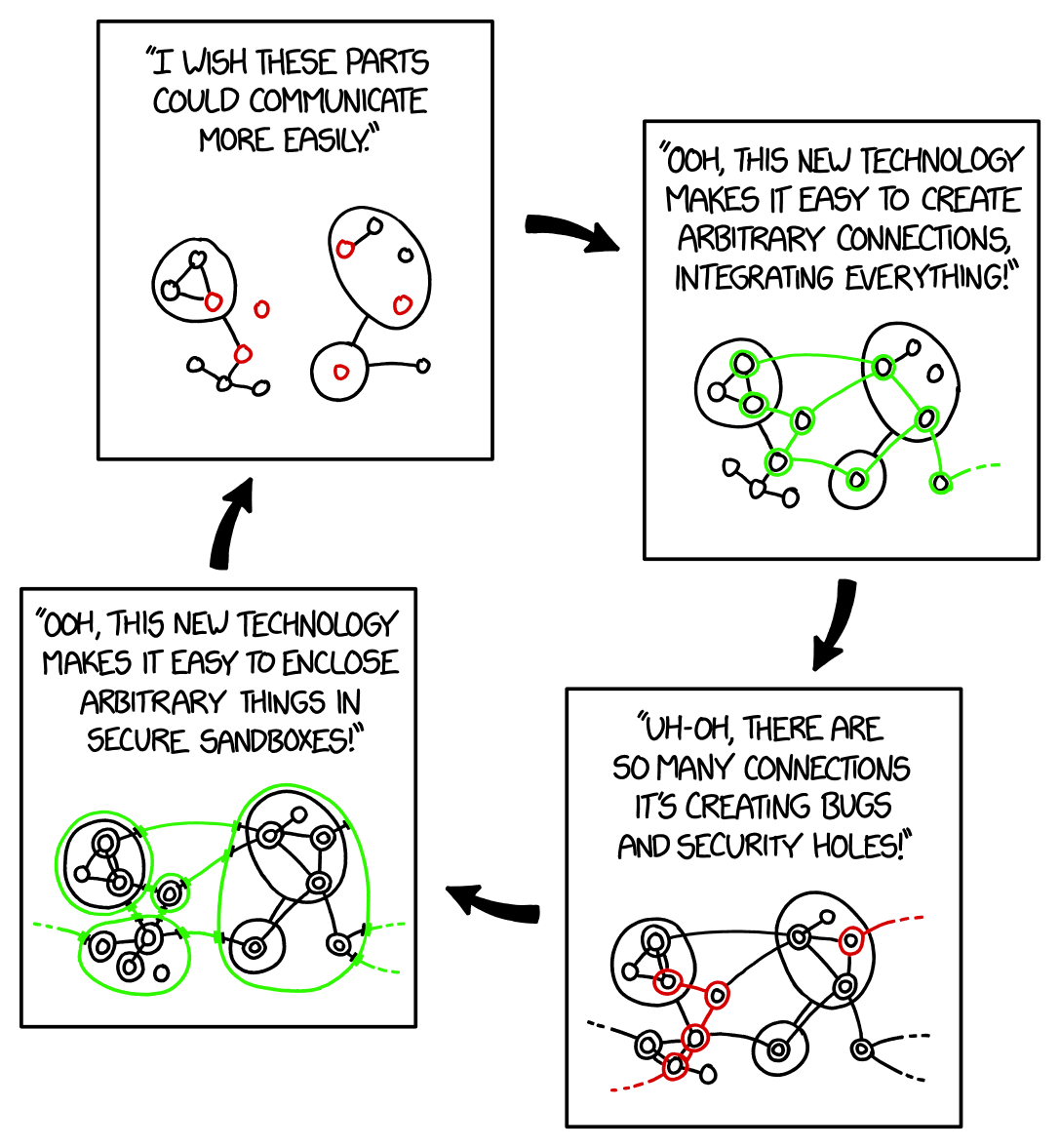
Container
Just Put It in a Box
Application Logic Sandbox
Reasonable Applications
Permissions
Define Command Exposure
[[permission]]
identifier = "my-permission"
description = "Reading files is only exposed on Windows"
platforms = ["Windows"]
commands.allow = [
"fs:read_file"
]
Scopes
Define Fine Grained Access
[[scope.allow]]
path = "$HOME/*"
[[scope.deny]]
path = "$HOME/secret"
Capabilities
{
"identifier": "mobile-capability",
"windows": ["main"],
"platforms": ["iOS", "android"],
"permissions": [
"nfc:allow-scan",
"biometric:allow-authenticate",
"barcode-scanner:allow-scan"
]
}
Isolation Pattern
Frontend Developer's Hidden Power
Content Security Policy
First Layer of Defense
default-src 'self'; connect-src ipc: http://ipc.localhost
Application Development Lifecycle Threats
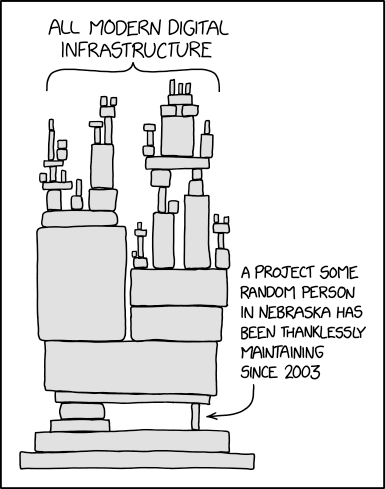
The Weakest Link Defines Security
Upstream
The Fragile Shoulders You Stand on
Upstream Rust
cargo audit, cargo auditable, cargo vet, cargo crev & cargo-supply-chain
Upstream JavaScript
npm audit
That's it?
Development
It's Your Responsibility
IDEs
Code Execution Everywhere
main.rs
fn main() {
// Super safe to run me!
println!("Hello, world!");
}
Hello, world!
PWNED?
warning: rust-build-demo@0.1.0: PWNED
Hello, world!
build.rs
fn main() {
println!("cargo:warning=PWNED");
// go wild here
}
Secrets
A Developers Nightmare
dev.env prod.env idontknow.env
Build
Trust, Trust, Trust?!
Reproducible
The Same As Always, Please!
Production Secrets
# Keep This Secret!!!
PROD_SECRET="Correct Horse Battery Staple"
Runtime
It's Too Late Now, But it's Okay